Pompompurin and BreachForums
Something more than a year has passed since Pompompurin was detained by the FBI. I did this investigation on him when it happened, and now after some time, I’ve decided to make it public here.
The goal of the investigation was simple, I just wanted to find who pompompurin was, how he became the creator of BF (BreachForums) and how he ended up detained (bad OPSEC as usual :)). Keep in mind that everything you are about to see is Open Source.
The starting point of this investigation was his username “Pompompurin”, that if you search for it, you will see it’s a Japanese cartoon character, a golden retriever dog created by the company Sanrio in 1996.
As you may imagine, an initial scan of the nickname reveals a substantial number of results across various platforms and social media. Upon filtering through all these results, I found an inactive SoundCloud account with interesting links. Here is where the actual investigation starts.
The first link directs to a Twitter account (user: @xml), while the second link leads to a website accessible at the URL https://pompur[.]in/.
1. The pompur[.]in site
The website, located at the URL https://pompur[.]in/, provides an extensive range of information concerning the user known as "pompompurin”:
We can confirm that the Twitter account (@xml) linked to the SoundCloud profile is the same as the one provided on the website. Additionally, other contact methods for reaching the user pompompurin are shown, including a Telegram account (@paste), a Mastodon account (@pom), and a Matrix Project account (@pom:pompur.in). The email address pom@pompur.in is prominently displayed, indicating a direct association with the user's personal domain.
Further research into the domain pompur[.]in revealed the following:
Registered by Tucows Inc. on 2021-04-30.
Associated emails:
pom@pompur.in
pompompurin@riseup.net
An IPv4 address (198.251.84.20) associated with the domain pompur[.]in traced to the location of Bissen, Luxembourg. (It is noteworthy that this IP address is provided by the same Internet Service Provider (ISP) that is responsible for supplying internet connectivity to a significant portion of the BreachForums network.)
Both the email and the domain have a direct connection with breached[.]vc
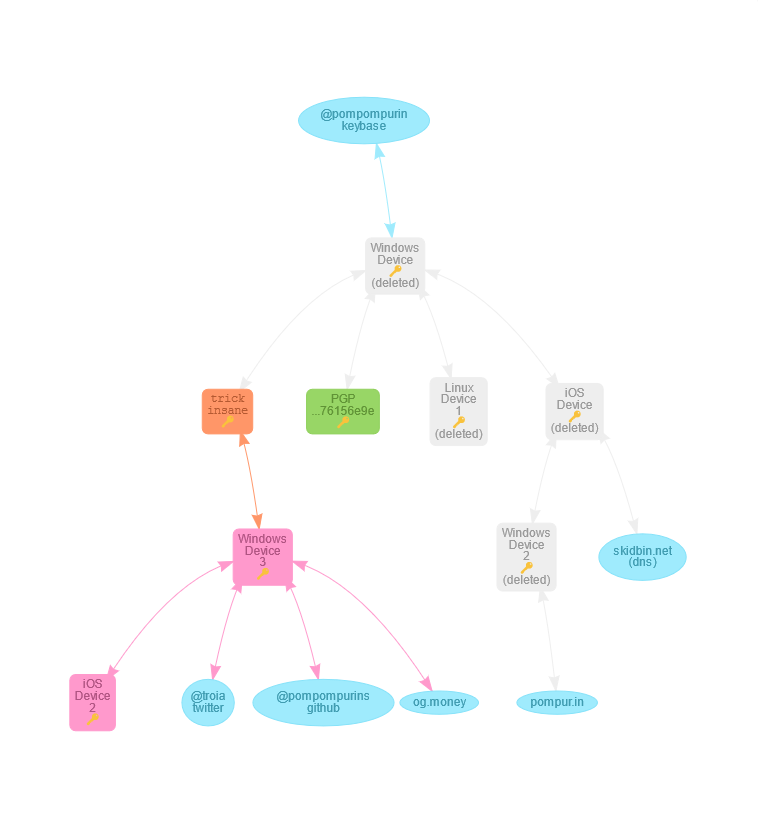
At the top section of the page (figure 2, pink), a link leads to his Keybase account.
A significant amount of critical information is available there, which will play a crucial role in the process of verifying the identities associated with this individual later. Such details include:
Same PGP key as the one in his website.
Three Windows devices and a Linux one.
Two iOS devices.
A GitHub account by the name “pompompurins”.
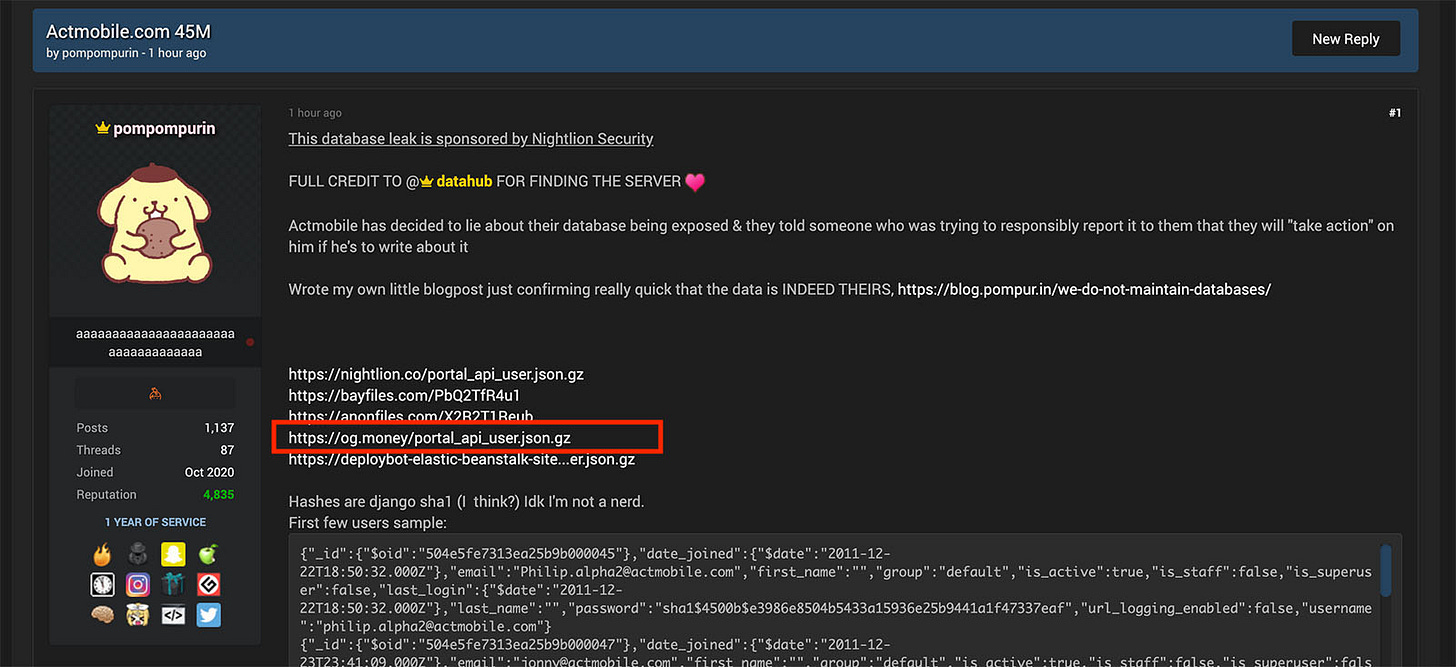
The domain og[.]money, which was used by pompompurin to disclose the ActMobile/FreeVPN database breach. Figure 4 captures the instance when pompompurin published the breach on RaidForums.
A Twitter account (@troia), which appears to be suspended as of the current date. This was a meme account about Vinny Troia, a cybersecurity researcher with whom Pom had some beef.
Upon examining a snapshot from December 2021 of the account (figure 5), the following can be observed:
He had a previous Twitter account (@pompompur_in) that got suspended.
His webpage is linked in the bio.
The individual refers to an "old Riseup" email domain (riseup[.]net) in Figure 6, which we have previously identified as being connected to the pompur[.]in domain. This suggests that prior to acquiring the pompur[.]in domain and transitioning to the new email, the individual likely used pompompurin@riseup[.]net. This information holds significance in the investigation, particularly in relation to the individual's involvement with RaidForums (see figure 8).
Returning to the pompur website, two notable links (highlighted in yellow in Figure 2) direct to pompompurin's profiles on the Russian forums exploit[.]in and xss[.]is.
And finally, a link to his profile on BreachForums, where he not only holds membership but also is identified as the founder and administrator (Figure 7).
2. RaidForums
The first recorded appearance of pompompurin dates back to October 26, 2020, when he joined Raid Forums using the email address pompomurin@riseup[.]net. This information was later confirmed by the FBI in the Pompompurin Affidavit No. 1:23-mj-67.
In Figure 9, the first available snapshot of pompompurin's profile (January 26, 2021) can be observed, thereby corroborating the previously mentioned registration date on the forum.
Pompompurin maintained a consistent daily presence on the forum, actively engaging in discussions with an average of 2-3 posts per day. He was responsible for orchestrating numerous data leaks, which were subsequently published on the forum. These significant data breaches contributed to pompompurin's growing reputation, and helped to establish BreachForums as the best alternative following the seizure of RaidForums. Let’s see some of the most important ones:
2.1. Leaking US PII
On April 22, 2021, pompompurin leaked a database containing personally identifiable information (PII) of 2.5 million Americans. The leak included full names, date of birth, email addresses, phone numbers, home addresses, marital status, political affiliation, salary, and other private details about US residents. This massive leak was approximately 263 GB and contained about 1255 CSV files and 59 million unique e-mails.
2.2. Robin Hood
Also, in early November 2021, pompompurin hacked the investing company Robin Hood. The breach initiated with a social engineering attack directed at one of the company's customer support employees.
Through this attack, pompompurin successfully gained access to the customer support platforms used by Robin Hood, allowing him to collect the email addresses and full names of approximately 7 million customers.
Subsequently, pompompurin made attempts to sell the compromised data on RaidForums. Additionally, he claimed to have harvested customer IDs from Robin Hood, although these were not offered for sale at that time.
2.3. FBI email hack
On November 13, 2021, pompompurin compromised the FBI’s external email system, sending thousands of messages warning of a cyberattack by cybersecurity researcher Vinny Troia, who was falsely suggested to have been identified as part of The Dark Overlord hacking group by the US Department of Homeland Security.
The emails were sent to addresses taken from the American Registry for Internet Numbers database and it was reported that the hacker used FBI’s public-facing email (eims@ic.fbi.gov), which made the emails appear legitimate.
By the same time, Brian Krebs from KrebsOnSecurity received a message from the same email address: “Hi its pompompurin, check headers of this email it’s actually coming from FBI server. I am contacting you today because we located a botnet being hosted on your forehead, please take immediate action thanks.”
This was one of the most infamous hacks of pompompurin, and the one that gave him the most recognition on the underground community. It is important to note that pompompurin was involved in numerous other security breaches that were posted on RaidForums, which have not been fully covered in this report.
3. BreachForums
3.1. The creation of BF
On the 25th of February 2022, users were no longer able to successfully log into the RaidForums domain. On the same day, a prominent moderator from the forum, Jaw, posted to the forum’s Telegram that the raidforums[.]com domain had been seized, and the current website domain was run by law enforcement as a honeypot.
Another RaidForums moderator, moot, locked the chat and Jaw suggested rf[.]to would be the new domain for future RaidForums operations. It’s unclear how Jaw confirmed the seizure of the RaidForums domain. Some speculate Omnipotent was allowed to call from inside police custody and notified Jaw directly. As today, the rf[.]to domain is holding a message from Omnipotent, as seen in figure 15.
With the arrest of Diogo Santos Coelho, aka. Omnipotent; and with the announcement that raidforums[.]com domain had been seized and was now a honeypot, pompomurin intentionally DDoS attacked the domain to prevent users from exposing themselves and to limit the FBI’s success in obtaining the credentials they sought by keeping the domain alive.
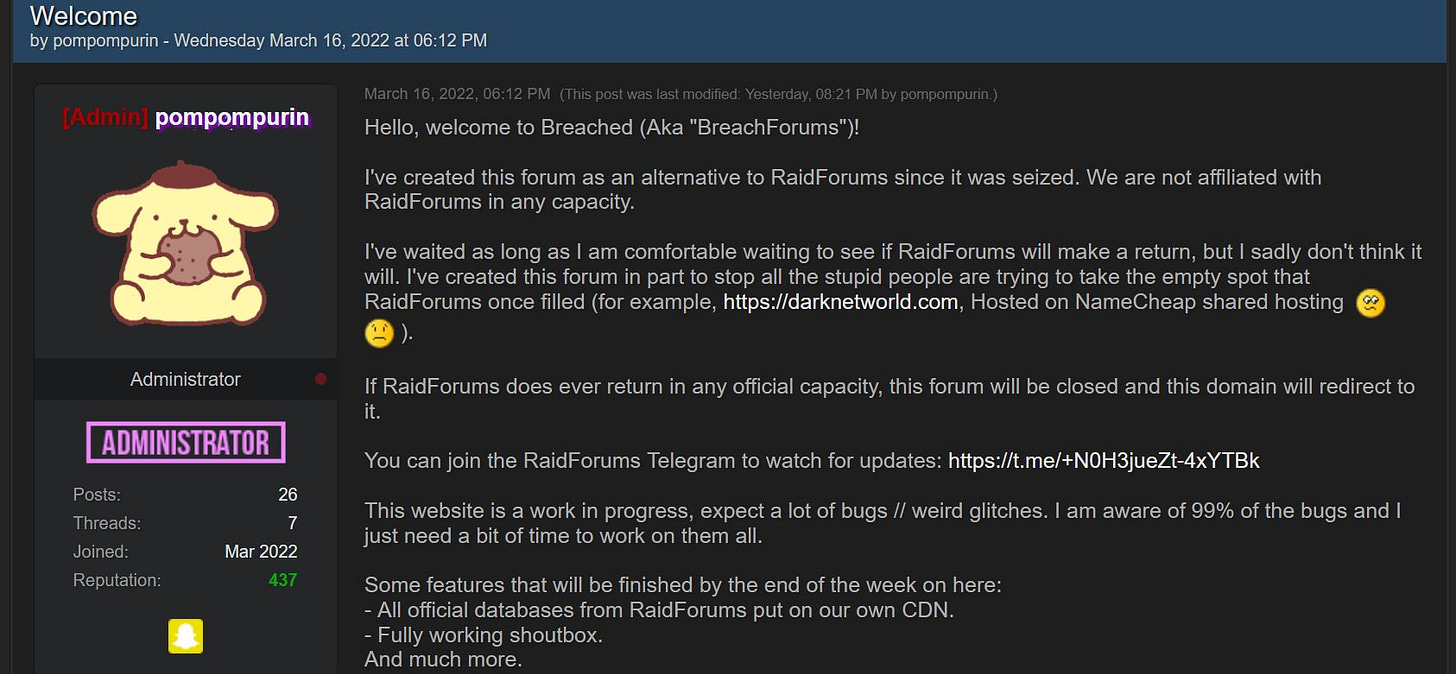
After a month of anticipation and with the domain remaining inaccessible, pompompurin made the announcement of BreachForums (figure 17) as an alternative platform for all RaidForums users. In the announcement, pompompurin assured users that their ranks would be preserved, and promised to migrate all the official databases from RaidForums to the new platform, even adapting the frontend of the website almost identical to the one RaidForums had. This move aimed to provide continuity and a familiar environment for the RaidForums community, while also establishing BreachForums as a successor platform.
An interview on or about March 16, 2022, on the website dataknight[.]org, reaffirms the intentions pompompurin had with BreachForums, and quote “I have a trusted person who will have full access to everything needed to relaunch it without me” in case he was arrested. This person will probably be Baphomet, which will be introduce later in section 3.3.
3.2. The structure
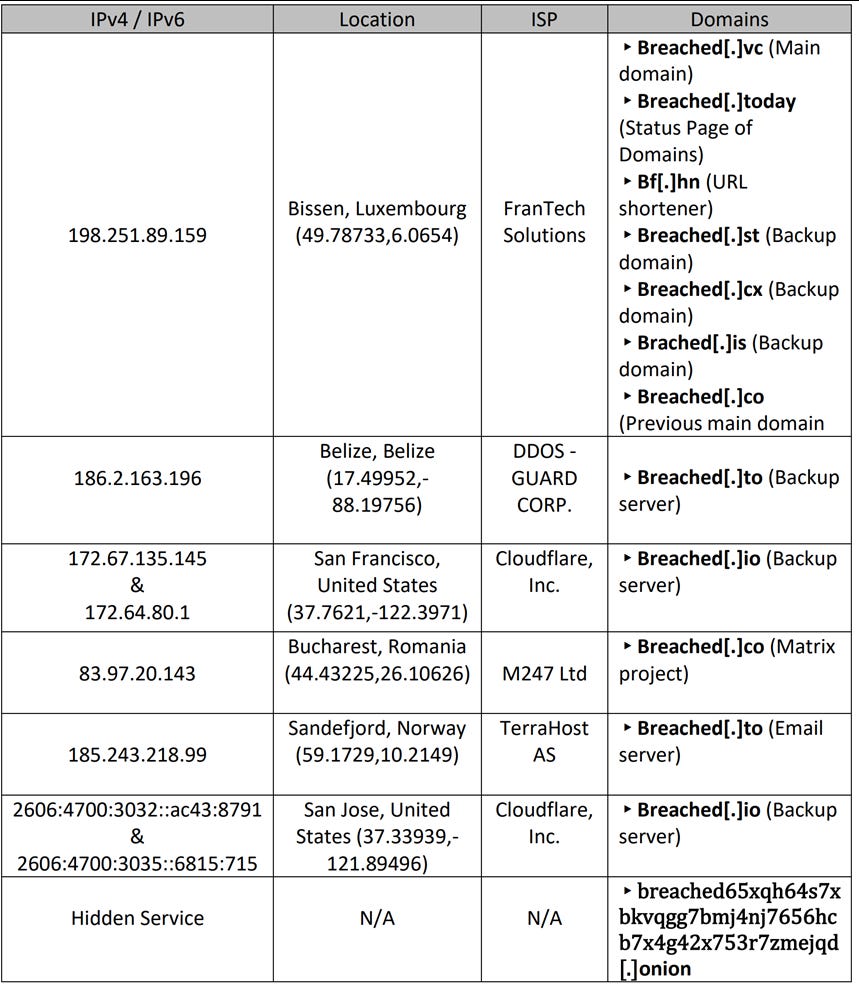
BreachForums had a fairly robust structure behind, with several backup domains and dedicated services.
Detailed information about pompompurins activity on BreachForums can be found at the FBI document: Case 1:23-mj-00067-JFA Document 2 Filed 03/15/23.
3.3. Shutdown of BreachForums
After one year of BreachForums being operational, boasting an approximate user base of 300,000 individuals, its founder, pompompurin, was arrested. In an affidavit filed with the District Court for the Southern District of New York, FBI Special Agent John Longmire said that at around 4:30 p.m. on March 15, 2023, he led a team of law enforcement agents that made a probable cause arrest of a Conor Brian Fitzpatrick in Peekskill, NY.
Two days after the arrest, an admin of BreachForums called Baphomet, announce the highly probable arrest of pompompurin, and states that he will be the one taking the ownership of the forum, and suspend all pompompurin’s important access for safety.
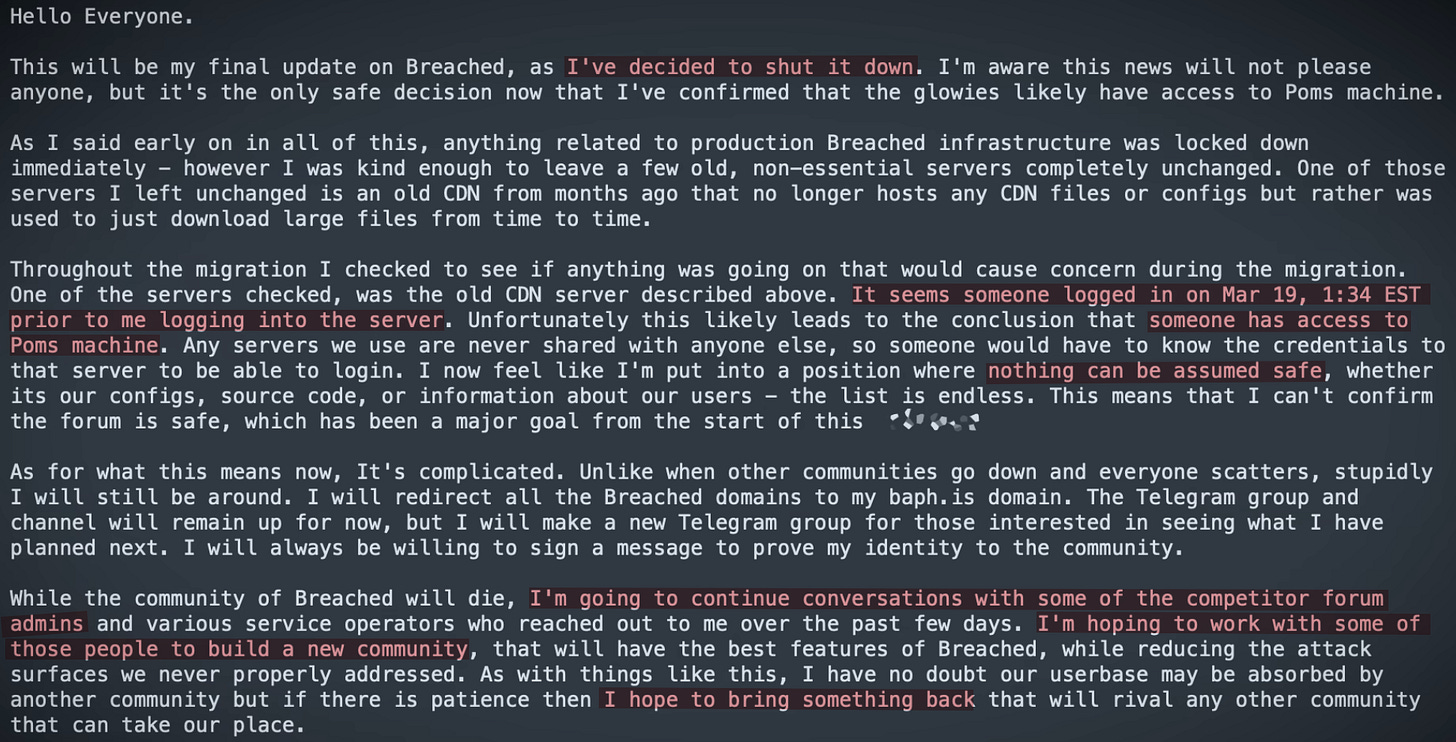
Baphomet initially stated their intention to maintain the continuity of the forum and migrate BreachForums to a new infrastructure, as indicated in Figure 21. However, their plans took an unexpected turn on March 21, 2023, when Baphomet confirmed that the FBI had gained access to pompompurin's machine. Consequently, Baphomet made the decision to shut down the forum, as depicted in Figure 22.
Edit 05/2024: When redacting this report, no more updates were made since April 19, 2023 on his “BaphometOfficial” Telegram channel, neither in his website baph[.]is; but as you may know for now, BF is currently running under Baphomet administration.
After the seizure of BreachForums at that time, it was observed that certain data and user profiles from the platform were appearing in other popular forums like XXS and Exploit.
4. Conor Brian Fitzpatrick
4.1. Attribution of Conor Fitzpatrick as “pompompurin”
After the seized of RaidForums, the FBI took control of the infrastructure, and access all the data it contained. Upon investigation of pompompurin’s activity inside the forum, a private conversation with the owner Omnipotent, on November 28, 2020, stands out.
On it, pompompurin specifically mentions to Omnipotent that he had searched for the e-mail address conorfitzpatrick02@gmail.com within a database of breached data from “ai.type” (company that was victim of a breach of its database around December 2017), but he wasn’t finding it, suggesting that the database was incomplete, because HIBP (Have I Been Pwned) did show the email.
Even though he tries to deceive Omnipotent to think that it’s not his actual email, it seems very clear that it looks like “my old email” that he’s referring to.
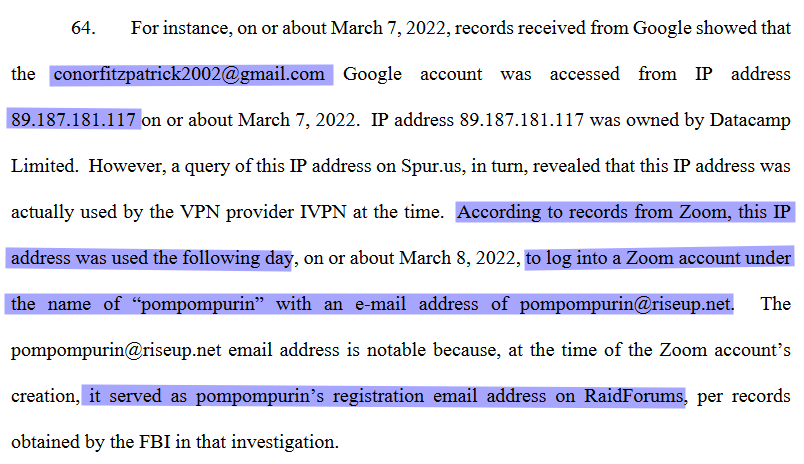
According to some Google records months previous to that private conversation with Omnipotent, the FBI saw that conorfitzpatrick02@gmail.com Google Pay account share the same details as another email: conorfitzpatrick2002@gmail.com .
As shown above, the old email that replaced the new one, shared the same name, physical address and Visa card ending in 3068. This accounts also had two of his personal cell phones registered, an iPhone 11 Pro Max, and an iPhone 7 Plus. This information confirms that these devices were also registered in pompompurin’s Keybase account.
These two devices, at some point had used the same phone number, ended in 3144 (figure 27), and the RaidForums logs shows that at least 9 IP addresses registered with that same number, were used to access pompompurin’s account.
The FBI also found that pompompurin’s new gmail account conorfitzpatrick02@gmail.com was accessed using the same IP address as his Zoom account, registered with his pompompurin@riseup.net email, the exact same one that he used to log into RaidForums.
At last, the recovery email register with the conorfitzpatrick02@gmail.com account, funmc59tm@gmail.com was created using the IP: 74.101.151.4, which was register at the name of pompompurin’s father, at their physical address.
4.2. Conor’s real identity
Limited information is openly available regarding the true identity of "pompompurin" and associated social accounts. However, conducting research using the individual's full name brought some findings, including an address, age, and a phone number. Notably, the phone number registered by the FBI concludes with the digits 3144, suggesting that the current phone number, (914) 699-9668 may be a different one used by Conor (figure 27).
The age of 20 is supported by both FBI records and the years referenced in the individual's Gmail accounts, providing some corroboration.
In order to verify the accuracy of the provided address, a reverse image search was conducted using images from two news channels that reported on the arrest of "pompompurin." The first news channel is News 12 Westchester, which covered the arrest on March 15, 2022. The second source is the local Peeksill Herald, which reported the news on March 19, 2022.
No social media profiles owned by Conor B. Fitzpatrick featuring his appearance were found during the investigation. However, an interesting clip of images of Conor B. Fitzpatrick was found on a webpage, with no source confirmed.
Additionally, a YouTube video of the 2021 Peekskill High School graduation ceremony featuring someone named Conor Brian Fitzpatrick was located. On the video, his name is mentioned at 8:37, and appears on camera at 9:19.
Comparing the Youtube video with some images taken from the official Peekskill High School graduation ceremony video, uploaded at their website, as well as the graduates list, confirms that Conor was present that day.
At a doxbin[.]com page, a lot of high valuable information it’s found (figure 41 - partially blur for privacy).
As it is not a fully reliable source, we carry out detailed research on the displayed data to confirm its validity:
The physical address matches all the registers already proportionated, and also the address on the mother’s webpage (figure 42).
Two of the three phone numbers are corroborated: ended in 3144 from Verizon (FBI records), 9668 registered at fastpeoplesearch[.]com (figure 30), and a new one ended in 5399.
All his social accounts and emails matches the ones already covered.
The connection of Mary M. as the mother of Conor can be checked at his social media profiles (figure 43), website (figure 42 and 45) and the YouTube account where the graduation video was uploaded (figure 44):
The connection of Mark E. as the father of Conor can be checked at his twitter account (figure 46), and also at his wife’s serveral Instagram family photos:
Aditionally, on the 28th of May, 2023, The U.S Postal Inspection Service (USPIS) posted a public notification, listing the multiples Conor Brian Fitzpatrick’s properties seized (figure47).
5. Conclusion
Conor was charged for his involvement in the theft and sale of sensitive personal information belonging to “millions of U.S. citizens and hundreds of U.S. and foreign companies, organizations, and government agencies” on the Breached cybercrime forum.
Fitzpatrick appeared in court in the Eastern District of Virginia after being arrested one week before at his home in Peekskill, New York, and released on a $300,000 bond.
As for today, the exact whereabouts of Conor are unknown, but BreachForums is up and running under the administration of Baphomet, although I have my suspicions that it could be an FBI honypot.












































Wow, as a beginner to OSINT, this was an amazing post on what is possible. Thank you so much.
kontol